We live in the world where our lives are bound to technology and each click, swipe, and key stroke is tracked. But so, what occurs when those computer tracks lead to evidence in a crime or a company scandal? Get to know the exciting field of computer forensics--the area that helps to make visible what was previously unknown. Based on the detailed tutorial of William Oettinger, Learn Computer Forensics (Second Edition), this paper will discuss the complexity of searching, analyzing, obtaining, and preserving digital evidence. As an amateur detective or become inquisitive about the inner mechanics of digital detectives, you will be ready to enter a space when bytes can crack cases.
The Essence of Computer Forensics: Decoding the Digital Realm
Computer forensics or digital forensics may be defined as a systematic procedure of discovering and analyzing electronic evidence to aid investigation. It is like going deep into the computer system and discovering something new; something that has never been realized before as aptly expressed by Oettinger in his book. In contrast to classical forensics, which concentrates on tangible evidence, such as fingerprints or DNA, this aspect has to contend with dynamic digital evidence that may disappear after one power outage.
The field has gone at a fast pace in the 21st century, with almost everything being related to an electronic gadget. Digital evidence is everywhere but vulnerable, whether it is smartphones, or servers. This underlines the idea that there is no previous intense understanding of the functioning of the operating system and file structures to begin with, which makes the work accessible by both law enforcement and security units of a corporation, as well as to the private investigators.
Types of Computer-Based Investigations: From Crime Scenes to Boardrooms
Computer forensics does not exist within the shonky hacker territory; it exists across a continuum of situations. Oettinger classifies them into criminal and corporate investigations which have their own challenges.
Criminal Investigations
Digital evidence can either break or make a case in the criminal arena. Crime scene technicians, investigators and first responders have key roles to play. As an example, with illicit images, stalking, and similar cases, forensic specialists can go through devices to trace suspects to activity. Oettinger singles out the stalking crime in which electronic footprints such as emails or GPS locations can tell of trends of harassment. Likewise, criminal conspiracies tend to leave footprints in chat records or in encrypted documents.
The practical sense of urgency is evident in the Dennis Rader (BTK Killer) case, where the metadata tag of a floppy disk resulted in his arrest, or the Silk Road dark web market, which was brought down due to traced Bitcoin transactions and server logs. Terror attack in San Bernardino was associated with decrypting locked devices to extract motives, and the cases of intellectual property theft are based on procurement of stolen files on corporate networks.
Corporate Investigations
At the corporate level, forensics addresses the misconduct of the employees, spyware and insider threats. Imagine a worker stealing trade secrets through USB drives- Oettinger expounds how investigators retrieve deleted files or file history. The social engineering security threat or threat actors (such as hackers using phishing) require prompt digital autopsies to counter the harm.
The Forensic Analysis Process: A Step-by-Step Blueprint
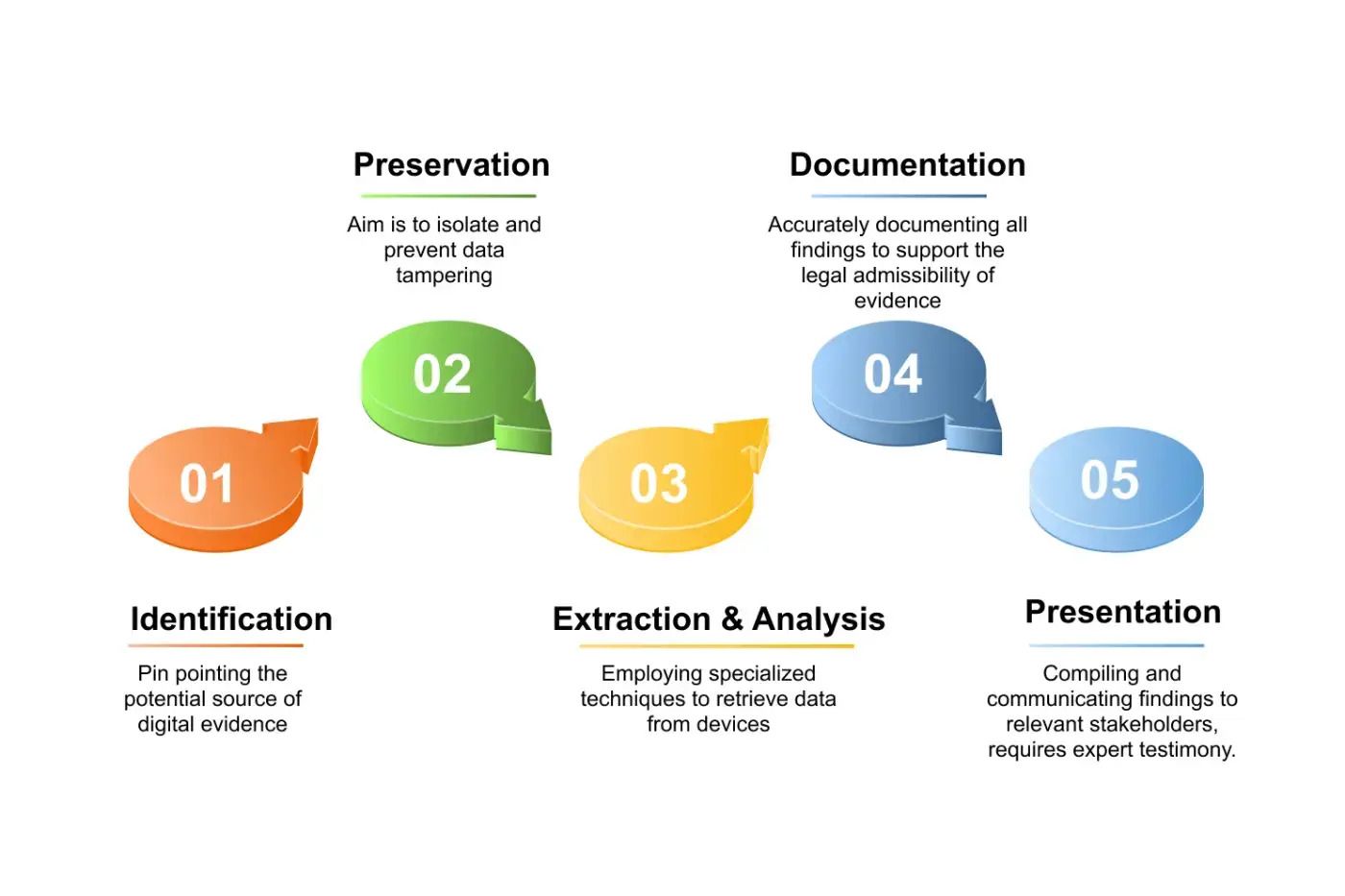
The core part of computer forensics is a systematic procedure to achieve evidence integrity. In her book, Oettinger divides it into pre-investigation considerations, data acquisition, analysis, and reporting, with complete focus on critical thinking of each individual case.
Essential Guide to the Digital Forensics Process | Fidelis Security
Pre-Investigation and Acquisition
Preparation is key. The investigators create a forensic workstation, response kit (with write blockers and sterile media), and programs such as X-Ways or Plaso to analyze the timeline. Chain of custody is one of the legal problems that are of paramount importance to prevent claims of evidence tampering.
Acquisition is the process of producing an exact duplicate of devices without modifying original devices. Such tools as hardware write blockers or software such as EnCase guarantee accuracy. Oettinger cautions against volatility: "The digital evidence is one of the hottest evidence that an investigator can deal with. Some of them are validating tools, forensic images (DD or E01), and to treat encrypted data carefully, no longer dragging the plug off running systems, and lose data in the RAM.

10 Useful Digital Forensics Software in 2025
Analysis and Reporting
After acquisition, it gets into the file systems (NTFS or FAT) and retrieves deleted files that were present within slack space as well as examining other artifacts such as Windows Registry keys or thumb caches. Timeline analysis software rebuilds the events, whereas media analysis and string search reveal secret data.
Making a report is the clincher: factual, detailed reports with conclusions so that non-technical readers, such as juries, can understand the result. Oettinger emphasizes on incorporating the five Ws (who, what, when, where, why) to attach activity to users. Investigator Arsenal: Tools and Techniques.
Tools and Techniques: The Investigator's Arsenal
Between boot processes in computer systems to the analysis of artifacts (user profiles, login times, file knowledge) in windows the book also provides readers with practical knowledge. Hash analysis, file signature, and antivirus detect malware by techniques such as checking the integrity of data, detecting disguised files, and file signature methods.
To have practical learning, data carving and email analysis practice underpin concepts. The more advanced issues include UEFI versus BIOS booting, master boot records, and host-protected areas- guaranteeing the examiners the control of the environment starting with the seizure till the courtroom.
Real-World Case Studies: Lessons from the Trenches
The Metadata of a mere Microsoft Word document revealed the identity of the killer, in the Dennis Rader case. Silk Road seizure consisted of forensic imaging of servers to follow anonymous transactions. The San Bernardino case brought into the limelight the issues related to encryption, as new strategies need to be acquired. Insider exfiltration is frequently revealed by the theft of intellectual property via USB logs or cloud logs.
These snapshots highlight one important lesson; when used appropriately, Digital evidence can reverse the fortunes of justice.
Why Computer Forensics Matters More Than Ever
Computer forensics cannot be done without in a world where cyber threats are on the increase. It is not only about the crime solving as Oettinger writes, but it is about our future in the digital world.
The profession requires accuracy, morality, and imagination whether fighting child exploitation or corporate espionage.
Technology Writer by OceanStack, Published December 29, 2025.